-
Reading Thucydides
Back in 2008 VoxDay lead a reading group through The Peloponnesian War by Thucydides. Along with discussion posts, he also created quizes and a ‘final exam’ for those following along.
The posts on Vox Popoli were all mixed in with his regular posting and the Blogspot search function leaves something to be desired. So I’m linking to all the posts and quizzes in order here to make it easier to follow along if others want to attempt this journey.
A quick note about Thucydides versions and books.
The Landmark Thucydides is by far the best version to read and follow along with. The maps alone make it worth while. The dates, page headers, index and glossary are also very helpful in following the story. I also have a Penguins Classic version which is dry and really hard to read by comparison. Consider making the Landmark version a priority.
Discussion and decision to read The Peloponnesian War.
- The world according to Vox [Out of order, but why we read history.]
- The Declining Value of Education
- I am Tempted
- The Voice of the People is Heard
- Overrated
Part 1
Part 2
Part 3
- Read Section 2.47 through 2.103 (To the end of Book 2.)
- Voxiversity: Thucydides S3
- Quiz 3
Part 4
- All of Book Three. Sections 3.1 to 3.116. It’s really quite a remarkable section, as it contains what must be one of the startlingly prescient passages in human history.
- Voxiversity: Thucydides S4
- Quiz 4
Part 5
- All of Book Four.
- Voxiversity: Thucydides S5
- Quiz 5
Part 6
- All of Book Five.
- Voxiversity: Thucydides S6
- Quiz 6
Part 7
- All of Book Six.
- Voxiversity: Thucydides S7
- Quiz 7
Part 8
- All of Book Seven.
- Voxiversity: Thucydides S8
- Quiz 8
Part 9
- All of Book Eight.
- Voxiversity S9
- Quiz 9
Final Exam
- Thucydides – the final
- Final Exam
- Of pseudos and the Peloponnesus [End of post announces those that finished the reading and exam.]
-
Private & Encrypted Communications
NOTE: Before I start here, I have to tell you: I am not an expert. I will not try to prove what I say here. I cannot help you with your tech issues and I can’t guarantee anything I say here is 100% true and safe. Do not trust me!
2nd NOTE: As I was researching and writing this article, and discussing it with friends, I slowly came to the realization that there is a high probability that anything I suggest here is either already compromised or could be at any time. Use the information below to make it harder for ‘them’ to openly monitor and silence you, but do NOT trust this with your plans to break free from their system.
I’m not sure there is any place left in the world where you can be 100% sure someone can’t hear or see you. Thermostats, appliances, vehicles … virtually anything electronic now often have either Bluetooth or WIFI (or both) and the software running those machines is often close source. They are watching and listening to you …
Make your freedom plans on paper. Communicate face to face or if that is not possible at least by snailmail paper. Don’t trust any of the systems below with your life or family.
OK … off we go.
As we watch Twitter, Youtube, Facebook (is anybody still on FB? Why???) and now Google banning thought and people that are not approved, we find ourselves in the position where we must employ tactics to protect ourselves or lose the ability to privately communicate with each other.
Twitter and Facebook both used their blocking powers to protect Biden and stop stories about his corruption from coming out during the 2020 Election. Twitter even went so far as to block people from privately direct messaging (DM) the story.
And then they banned the President of the United States of America and about 35% of his supporters.
These companies are not on our side. They do not support truth, and seem to be actively trying to destroy trust along with anything that is honest, true or beautiful. What they call Progressive is regressive in every way. Don’t believe their lies!
So we must employ ways to protect ourselves from them, or at the very least, make it much harder for them to shut us down, spy on us, or monitor our words for profit or for more nefarious entities. (If you think the 3 letter gov agencies are not monitoring domestic web traffic for certain words … well, good luck. See the Ed Snowden files about government spying on citizens for confirmation. After all, he did give up his freedom to tell us this.)
As I’m writing this, Twitter is busy banning and deleting freedom people and posts. Unbelievabe. Most People
The average person, for some reason, still believes that people and companies are inherently honest and good. Of course, that is what they are banking on … and I mean literally banking. They scrape, read, listen and watch virtually everything you do. From that data they build a profile and a social graph and can, with uncanny accuracy, predict what you want, who you want and what you are going to do next. And then they sell you. Not the real you, but the digital you is sold to whoever wants to buy you and own you. You become a slave of your own habits and characteristics and they use you for every cent they can.
Being sold to the highest bidder is the least of your worries though. It gets far darker. The governments of the world have almost always tended toward dictatorial control. Once a government leans that way, with what they already know about you through data collection, it is easy for them to find those that could oppose them. Once they decide what someone who is ‘unauthorized,’ looks like, they can search the data to find those people based on those characteristics. We have given them all our data … for free. They know exactly who and what you are, and they own you.
Lets say they decide that the ‘unauthorized’ ones are:
- Christian,
- land owners,
- who buy prepper and other ‘how to’ type books,
- and are friends with known unauthorized persons,
- and oppose ‘progressive’ and degenerate behaviour.
A simple search of the social graph database using those criteria will give them a list of the those the state could deem dangerous (based on those peoples abilities to oppose or simply live without the state.) This is the scenario that we should fear and hopefully avoid. (Having a blog like this … probably not a great idea. Hmmmm.)
Understanding this, should you be entering your data into their systems? Should you tell them what you are shopping for, who you are friends with … your hopes and dreams? Should you give them pictures of your home, your kids and places you’ve been. Should you have their machines listening to your every word while being in control of the systems of your home? (Alexa, Google Nest, Amazon Echo … etc.)
In this day and age of mass online communication (especially since the Covid Plandemic,) can we actually avoid telling them everything about ourselves?
The answer is … a solid maybe. You might not be able to cut them out of everything you do, but you can certainly mitigate the damage by making it really hard (and expensive) for them to monitor your communications.
Plain Text Everywhere
Eben Moglen Interview 2012. Full video here. Most people communicate with each other in plain text. They use cell phones to text. They use Facebook Messenger to plan meetings and family dinner parties. They use Instagram DM’s to flirt and find partners. They send emails by Gmail knowing that, in exchange for ‘free’ email service, Google will be reading and recording every word. In other words, the average person is undressing with the curtains wide open.
Why?
Well, I suppose it just easier that way. No need to hide if you have nothing to hide is the common answer. But as I’ve shown above, you DO have something to hide = you! You are the product. You are the slave. You are the human being trafficked. The easier you make it for them to see you in all your glorious nakedness, the easier it is for them to pimp you out for money … or worse.
The other issue (one I’m trying to help you through here,) is that encryption is hard to understand. Most of us just want to use our phones and computers … we don’t want to know how they work or how the nerds programmed them. Don’t bore us to death with the details.
Ok. Lets get into the good stuff.
Encryption for Chat Communication
1st of all. If you want to avoid all this encryption stuff, get rid of your phone and computer (and all the rest of the computerized stuff in your home and vehicle.) In my opinion, the safest and most private form of communication is still … zee pen and paper. You can write anything out and as long as you don’t have a camera looking over your shoulder, you can be assured it is private. If you can give that communication to the intended recipient hand to hand and they in turn, open and read it without a camera peering over their shoulder, you’ve just accomplished private chat communication. Realistic in this day and age? Nope. However, if you are really paranoid you can operate like this, and it works. (See 2nd EDIT above … you are probably not paranoid, just smarter than most!)
Not gonna use pen and paper? OK. Let’s move on.
About Federation
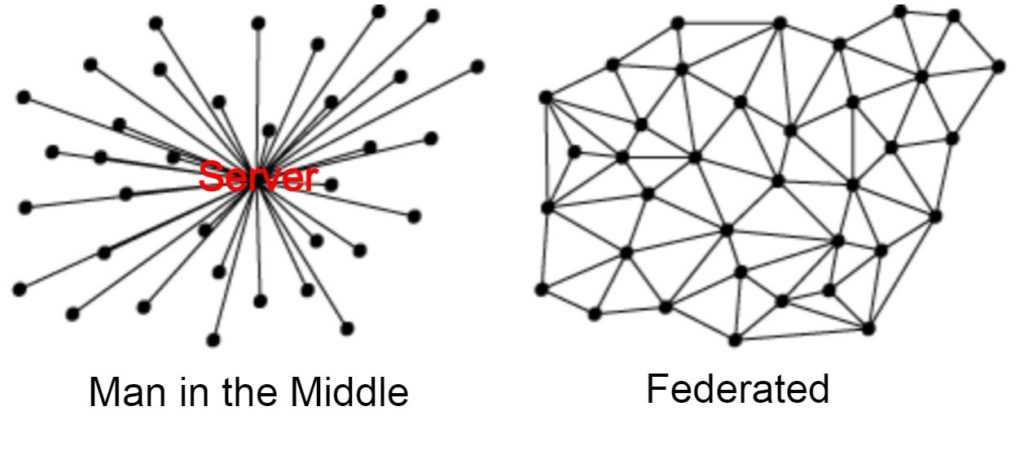
Before we begin, a quick word about Federation. Federated is not the feds coming for you. Federation, sometimes also called distributed networking is the distribution of communication without the need for a centralized server (or man) in the middle. Virtually all social media uses the man-in-the-middle approach to communication by using centralized servers to distribute the flow of data. You log into their servers, tell them everything and they relay the message onto it’s intended recipient. This is bad. It means that at any given time, you have to rely on their security and hope and pray that they are not storing more than what they are telling you. Federation on the other hand transfers data through multiple nodes and often via different paths from end to end. This is better as there is no single choke point where people can sit and vacuum up your data.
The one time that a man-in-the-middle is good is if you are ‘the man.’ If you own the server, and the server logs, then you are in control of that choke point. This is good. Be the man.
Lets Begin with the Worst
Assuming you don’t want everything you write to be plain text, then the next best thing is to use one of the mainstream ‘encrypted’ chat services. The big boyz on the block are:
- Telegram
- Signal
- FaceBook Secret Messenger (lol … no.)
- aaaannd a bunch of others all using the same model
I don’t recommend any of these. Here’s why.
They all do two things.
- They all put a man-in-the-middle by routing your messages through their central servers.
- And they all ask you to trust them to do the right thing.
Central Servers. Whoever owns the servers, owns the server logs. Review the video above to understand how important the web servers are. I suspect these messaging systems decided to allow encryption to be used at the ends because they knew that the logs in the middle were as important, or more important than what was actually being said. The social graph stays intact if they know who is talking with whom, how often and who is on your contacts list.
Trust. Remember how Google used to say, ‘Don’t be evil’ and then they turned out to be the most evil of the bunch? It’s the same with all of the above. They all want you to trust them. You have to trust that they won’t steal your keys, keep logs about who you are talking to and that they won’t give up your messages if the feds come knocking. You name it, they want your trust. This is not how encryption works. If I really trusted these companies, I would not be looking for encryption! To go back to the ‘undressing with the curtains open’ analogy, they are saying, ‘It’s OK to undress in front of us, we won’t look. We promise.’ Hard NO.
Let’s look at a few of these specifically.
WhatsApp. Owned by Facebook. Need I say anymore? I would not trust Zuckerberg any further than I could throw him. He literally hates half of the people who are his product, and would do anything to see them destroyed … but you can trust him with your encryption. It will be fine = No.
The 1st thing you do with WhatsApp is give them your cell phone number and profile pic. They then ask for your contacts list … which they will spam to tell everyone on your list that you just joined WhatsApp. Great. Thanks.
They also very helpfully offer the backup your messages for you … using Google Drive. So you end up giving Google a piece of your hot data action too. I wonder how much Google paid to get that cozy little deal? Not only that, but WhatsApp even tells you that once you backup your messages, they are no longer safe. No kidding! You just gave Google all your chats (hopefully still encrypted, but who knows,) who you’ve been chatting with, how often and when. Basically you’ve given them the server logs. Sharing your chat logs with WhatsApp AND Google … this is not good.
Further, WhatsApp has just announced (Jan, 2021) that they are going to link all your WhatsApp data to the Facebook data they have on you … yup, your encrypted chats including your contacts lists, how often and to whom you are chatting are all going into Facebooks social graph. Wonderful.
Telegram.
- Central servers
- Have to register with your Cell number
- Encryption is not default
- Encryption for regular messages is handled at the server level which means the server unencrypts your messages and re-encrypts them on the way out. Why??
- Their server side encryption protocol is closed source. This means that no nerds have inspected their code and we can never be sure what they are doing under the hood. But you can trust them, right?
- Based on trust. We won’t look at your messages … scouts honour.
- Will collect and keep your personal chat connections including IP addresses for up to 12 months (no problem though, trust us.)
Facebook Secret Messenger. First of all, would you please get rid of Facebook? Zuckerberg has done more to destroy your privacy than any single other person in the world. He hates you but as long as you give him all your private life info he is willing to make money from you. Here is what Zuck thinks about you and your privacy:

From Business Insider Still want to use his ‘encryption’ system? Don’t.
Signal. Signal is a unique communication app that might be somewhat better than the previous three. What signal does is replace your phones SMS system with their app. The one main drawback is that it requires you to use data instead of the cellular SMS system. (Here in Canada, data is expensive … very expensive. When you use Signal, it replaces your cellular SMS system and you need to have data enabled. This doubles the price of most mainstream plans in Canada. A huge drawback.)
Signal is easy to use and set up and everything pretty much runs quietly in the background seamlessly replacing SMS. However they still:
- Get your cell number (apparently the profile pic and user name associated with your phone number are encrypted … who knows. Based on trust.)
- Force you to use Google Play Store to get the app and have Google Play Services enabled on your phone. You know, the ‘don’t be evil’ people? (Google Play Services forces you into ‘features’ you don’t necessarily want or even know about. For instance, a Covid tracing ‘feature’ seems to be on the horizon.)
- Use Central Servers
- Ask you to trust that they are not storing messages
The owner of Signal Foundation, Moxie Marlinspike, is an intriguing man. He does not fit into the soft, puttylike mold that the Mark Zuckerbers, Twitter Jack’s and Bill Gates seem to have been poured from. For that reason alone I tend to trust him more … just not enough to get naked in front of him.
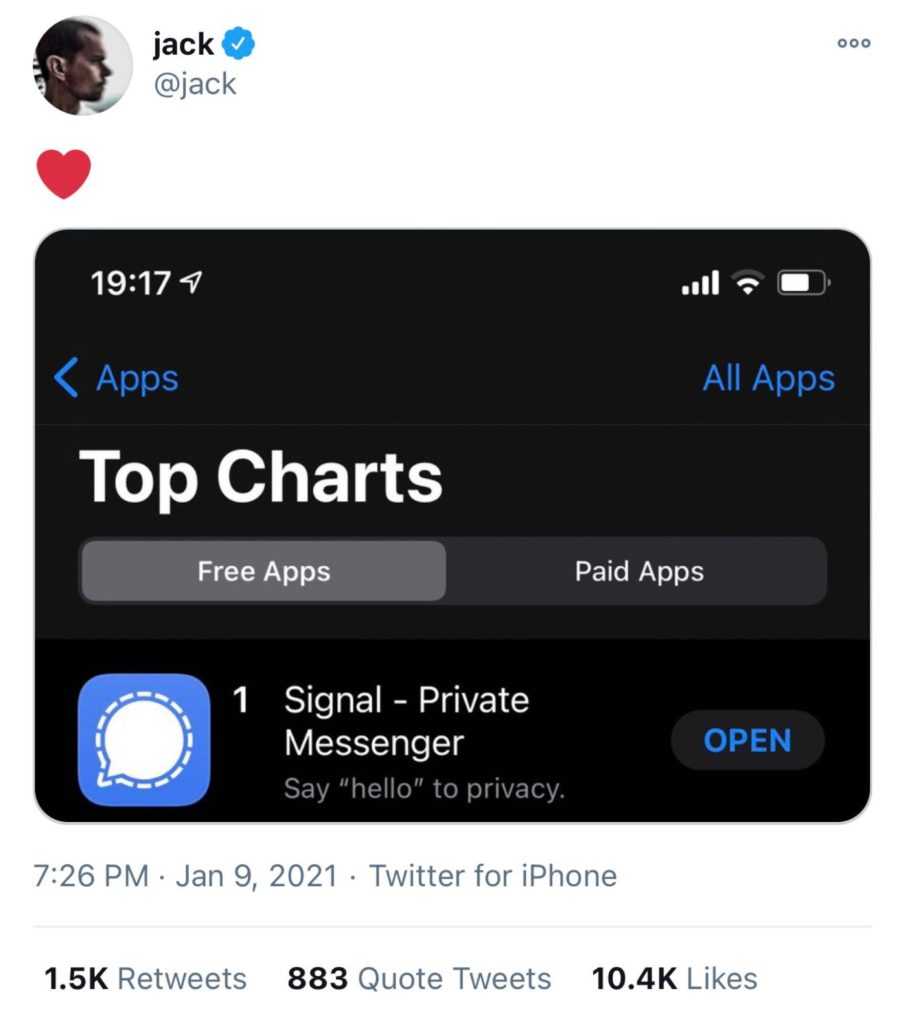
EDIT: Jacko from Twitter endorses Signal which is a HUGE warning flag. This was after Apple banned Parler from their app store. Apparently Jack was happy to see Parler go and not unhappy that Signal topped the charts. Not a good sign.
The Encrypted Chat System I Use
Here are the things I want to see with my encrypted chats.
- End to end encryption.
- Completely federated or at least routed through servers I own
- The only person I have to trust is the recipient of the message
- Open source so nerds can inspect the code for nefarious workings
- Don’t have to get it from ‘don’t be evil’ Google
- Don’t have to give up my cell phone number or Contacts list to some central server
- Not developed by people who hate me or want to own me
Enter Delta Chat.
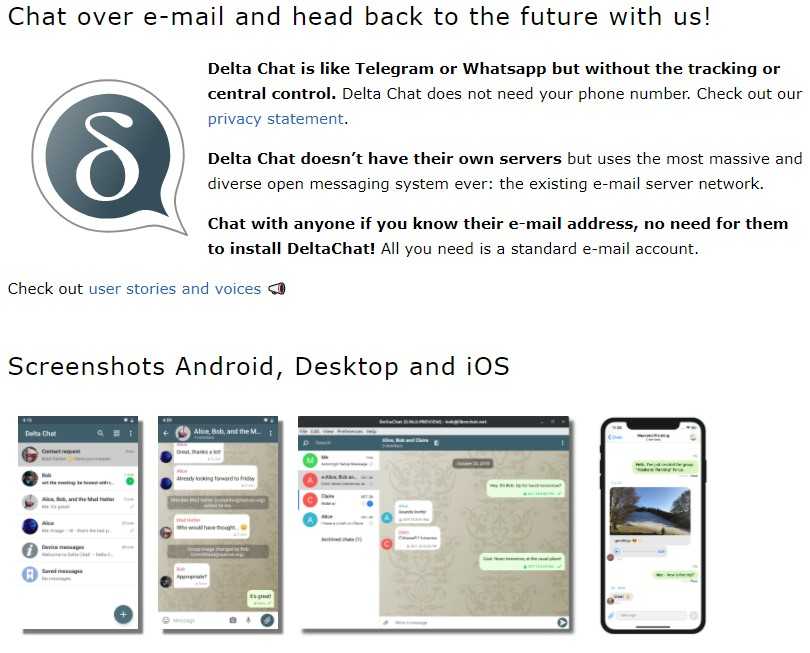
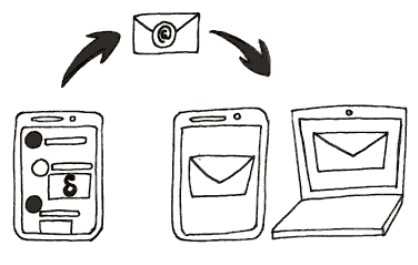
Delta Homepage Delta is an App that you either put on your phone or desktop that provides encryption. What makes them unique is that they use email to send the chat. So instead of your now encrypted message going through WhatsApp or Telegram servers, it goes to your selected email provider and from them through the email system to the intended recipient. Email is the largest federated system in the world, you might as well use it. Once the recipient gets the chat with Delta, their app unencrypts the message and they can read it.
So this is what Delta has done for us:
- Encrypted the message on your side (including the subject line, but not the header … more on that later.)
- Sent the message through a federated network = email
- Recipient gets to unencrypt and open on their own machine
Delta Pros:
- End to End encryption
- completely open source
- Distributed and downloadable from their website. You don’t need to ask Google to let you use it
- Does not use cell phone numbers
- Has no central servers
Delta Cons:
- Does Delta hate its users? Probably not, however, this question has been a little harder to figure out. They don’t seem to be beholden to any financiers that hate us. The people who are building Delta, while diverse don’t seem to be pushing any sort of agenda of indoctrination. The only thing I could find was this somewhat disconcerting post. However, that was the only one they posted along these lines and have since posted about more legitimate security and privacy issues such as those found in Russia and China. For now, I feel like I’m part of the group and not hated … lets hope that continues.
- The other Con is that I’m not sure about is Headers. Because Delta uses email, you email provider needs to know who your are sending the message to. So somehow we have to tell them. This info is not hidden. I wish the ‘from’ part would be hidden, but I don’t think that works with email transport. (I’m at the edge of my understanding of email transport here, so I’ll be happy to be corrected or helped with this … but I’m not putting anymore time into studying it. Nerd speak makes me crazy.)
In Real Life
My family has been using Delta pretty much exclusively for at least 3 yrs now. The system is completely robust. We exchange message chats, voice memos (like WhatsApp voice chat) pictures and videos. We have both family groups and private chats. It’s been great!
To add a level of security, we route our chats through my own email server. I use Yunohost and run the servers on a rented VPS. I own the server. I own the logs. I could delete it any time I want. The only thing better would be if I could host the server in my own home, but my ISP has made that very difficult at this point. I will fix that soon. (I’m talking to you Xplornet and your CGNAT.)
And that’s it folks. If you made it to the end = thanks! If you want to test a Delta installment with me, shoot me a email via my Contact Page and I’ll exchange emails with ya.
Finally, remember … don’t make your freedom plans online. Assume everything you say and write online will be surveilled.
-
Maple Syrup – Feed Your Own

This is the 1st post in what I plan to do as a series of posts about creating your own food supply.
This is how I harvest Maple sap and make my own Maple syrup.
Equipment

- I use food grade buckets that I picked up from a local grocery store bakery. I think I paid a buck a piece.
- For taps I’m using 3/8″ brass unions from my local hardware store. I notched the ends to create more flow but I have no clue if that really made a difference or not. Just made sense to me.

- I use 3/8″ hose to move the sap into the buckets.
Method
I use a hand drill (just because its easy) to drill a hole into my Maple at a slight upward angle and a little deeper than the half the union. The angle is to make the sap flow by gravity and slightly deeper than half the union so the union does not get plugged with wood when tapping in.
I use a hammer to tap the union into the tree till the center ridge tight against the bark which stops most sap from leaking out around the edge of the hole. Hose to bucket and let her run.
Boiling
For boiling I use an old ‘Pots and Pans’ drawer from a stove. Its porcelain so is smooth and nice and clean. It holds gallons and is wide so it has a lot of surface area for boiling.

I do this outdoors over an open fire with the pan between two cinder blocks. Feeding it hardwood slowly while watching the sap boil is very relaxing and cathartic … especially after dark with the moon in the background.
Finishing Syrup
I boil the sap down till it begins to thicken but not yet streaming from the spoon and then I transfer it to a pot and finish on the stove where I have more control over the temps. I don’t use a thermometer or hydrometer although I probably should. I use the old ‘sheeting off the spoon’ method which can be hit or miss – but the end product is just as good, just not exactly the same consistency. Basically, the the syrup ‘drips’ off the spoon in a stream, its done. I usually go for another minute or two just to make sure it’s thick, but that’s it. I’ll try to get a video or pictures of what it looks like at this stage. Going thicker is nice too – makes a kind of caramel which tastes amazing on ice cream or as drizzle on coffee cake. So thicker is not a bad thing.
Storage:
We usually keep our syrup in the back of the fridge, but if you bottle it hot, the lids will often seal and you can store it on any shelf. We picked up a couple of sealing bottles from Ikea to store ours in. (I’m not an Ikea fan by any stretch, but these worked great!)
-
2000 Hour Flashlight
Inspired by this little Kindle book I picked up the parts and assembled a couple of these flashlights today.
This is the stuff ready to assemble.
Prepped and ready for soldering. I chose to solder instead of glue as instructed by the book but only because I’m comfortable soldering and had the stuff on hand.
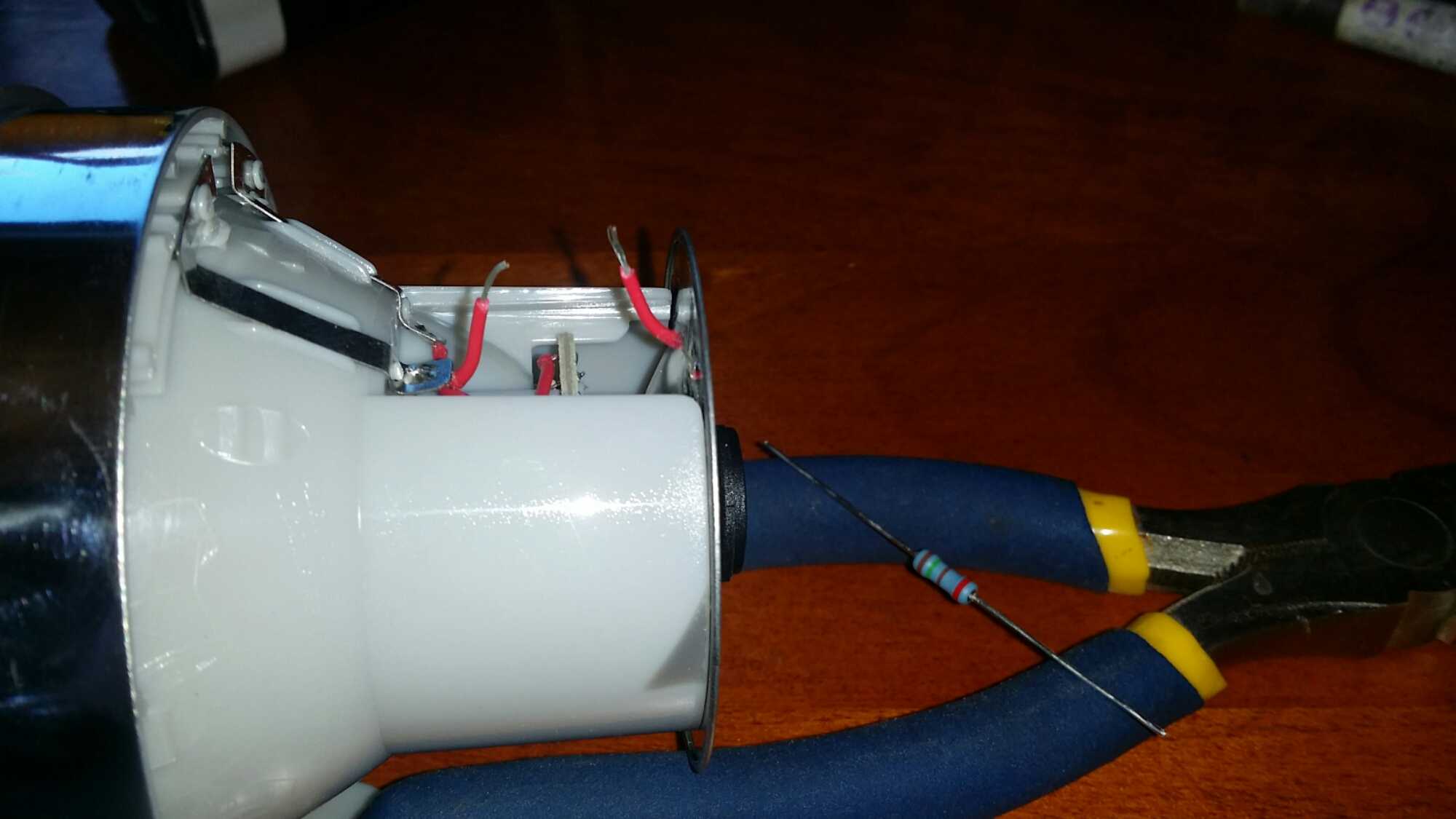
Resistor added and soldered in.
This is the difference between a moded light on the right and an original unmodified flashlight on the left. There is a substantial difference but the moded light is certainly usable. It is not what one would call a ‘thrower’ but still has plenty of light to work with.
I modified both lights I had and I’m leaving one on continuously to get a feel for really how long this light will go. The other I will use around the house and yard here. I’ll post an update when this little experiment is done.
All in all this is a very easy project and costs very little. If it ends up giving me a true 2000 hour light, I’ll be very pleased.
UPDATE – March 15, 2015.
I’ve left one of the modified flashlights on all the time since I made them back on Jan 12, 2015. I mean on as in, it’s never been shut off … just sitting there on my shelf in the kitchen burning away. That’s 63 days which equals 1512 hours and counting. The light had dimmed quite a bit but is still thowing out useable light. Pictures below show a comparison to the other modified light that has only been used a couple of times since I made it and also showing that it is producing usable light although the picture is not great. Will update again around the 2000 hour mark.
Here are the two lights side by side.
And … usable light!